Secure Vulnerability Dashboard
Business Opportunity
The security team responsible for managing vulnerabilities is facing difficulties in effectively summarizing and assigning a large volume of security issues. With a considerable number of vulnerabilities to handle and limited resources, the current process for triaging and allocating vulnerabilities is inefficient, leading to missed resolution Service Level Agreements (SLAs). A more efficient and streamlined approach is required to summarize and assign vulnerabilities promptly, ensuring that they are addressed by the appropriate team within the defined SLAs.
Link to Canvas Dashboard :Secure Vulnerability Dashboard
Solution / Approach
To address the challenges faced by the security team in efficiently managing vulnerabilities, we propose implementing a comprehensive solution that enhances vulnerability summarization and allocation processes.
The solution will include the following key components:
- Vulnerability Dashboard: Develop a user-friendly dashboard that presents vulnerability data in a grid-like manner. This dashboard will provide an intuitive interface for the security team to view, analyze, and manage vulnerabilities effectively.
- Summarization Features: Implement features such as sorting and filtering within the dashboard to enable quick and efficient summarization of vulnerabilities. The team can easily prioritize and categorize vulnerabilities based on severity, impact, or other relevant criteria.
- Collaborative Capabilities: Incorporate collaborative features within the dashboard, allowing team members to add notes, comments, or assign tasks related to specific vulnerabilities. This will facilitate better communication and coordination among team members, leading to faster resolution of vulnerabilities.
- Export Functionality: Include the ability to export vulnerability data from the dashboard in various formats (e.g., CSV, Excel) for further analysis or reporting purposes. This will support the team in generating comprehensive vulnerability reports or sharing information with stakeholders.
- User Authentication and Access Control: Integrate Single Sign-On (SSO) authentication to ensure secure access to the vulnerability dashboard. Implement role-based access control to separate different user groups and restrict access to relevant vulnerability data, ensuring data privacy and confidentiality.
By implementing this solution approach, the security team will benefit from a more efficient and streamlined process for summarizing and allocating vulnerabilities. The enhanced dashboard, collaborative features, and user authentication will enable the team to meet resolution SLAs effectively, leading to improved overall security posture and reduced risk for the organization.
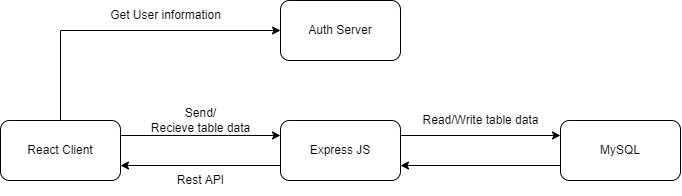
Architecture
Key Metrics
- Vulnerability Resolution Time: Average time taken to resolve vulnerabilities from assignment through the dashboard.
- SLA Compliance: Percentage of vulnerabilities resolved within the defined Service Level Agreements (SLAs).
- User Adoption and Engagement: Number of logins, frequency of usage, and interaction with collaborative features (notes, comments, task assignments) within the vulnerability dashboard.
- Dashboard Efficiency: Time taken to summarize and filter vulnerabilities within the dashboard.
- Exported Reports: Number and frequency of vulnerability reports exported from the dashboard.
By monitoring these key metrics, stakeholders can evaluate the effectiveness and efficiency of the proposed solution in managing vulnerabilities and meeting the defined objectives.
Tech Stack
- React JS
- Express JS
- MySQL
Resource Links
Feedback
We appreciate your feedback! Please provide us with any suggestions or improvements you have for our product.Please provide feedback on this product by clicking the following Link: